At first, I was really excited about the new version and was looking forward to seeing the new features in detail. But it looks like Cisco decided to follow its development cycle and release a new version without any significant new features.
New software features
Breakout port support with the Cisco N9K-C93600CD-GX and N9K-C9316D-GX switches
Dynamic and auto breakout ports are now supported with the Cisco N9K-C93600CD-GX and N9K-C9316D-GX switches.

Cisco Nexus 9000 switch secure erase
Cisco Nexus 9000 switches utilize persistent storage to maintain system software images, switch configuration, software logs, and operational history. Each of these areas can contain user-specific information such as details on network architecture and design, and potential target vectors for would-be attackers. The secure erase feature enables you comprehensively to erase this information, which you can do when you return a switch with return merchandise authorization (RMA), upgrade or replace a switch, or decommission a system that has reached its end-of-life.
This feature erases user data in the following storage devices:
- SSD
- EMMC
- MTD
- CMOS
- NVRAM

Support for BFD on secondary IPv4/IPv6 subnets
Bidirectional Forwarding Detection (BFD) is now supported for static routes that are reachable using secondary IPv4/IPv6 subnets that are configured on routed interfaces. This feature was originally introduced in the 5.2(4) release and is now available in the 6.0 releases.

Support for PTP G.8275.1 on remote leaf switch peer links and on vPCs
You can now use the PTP Telecom profile (G.8275.1) on virtual port channels (vPCs) and on remote leaf switch peer links.

Support for SyncE on vPCs and on remote leaf switch peer links
You can now use SyncE on vPCs and on remote leaf switch peer links.

Transport Layer Security version 1.3 support
Transport Layer Security (TLS) version 1.3 is now supported. This feature was originally introduced in the 5.2(5) release and is now available in the 6.0 releases.
Weight-based symmetric policy-based redirect (PBR)
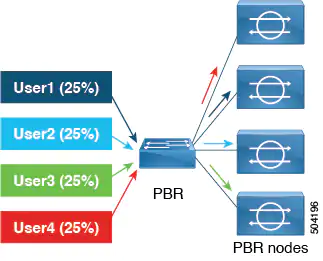
Prior to Cisco APIC Release 6.0(1), there was no option to specify a weight for each PBR destination. The capacity of the PBR destinations (service nodes) was not considered, and the weight for each destination was the same, which is the default value, 1. In the example below, consider four destinations, each destination could roughly receive the same amount of traffic because the weight for traffic load balancing is the same, approximately about 25% of the traffic.
| Destination | Weight | Traffic % |
|---|---|---|
| Destination 1 | 1 | 25 |
| Destination 2 | 1 | 25 |
| Destination 3 | 1 | 25 |
| Destination 4 | 1 | 25 |
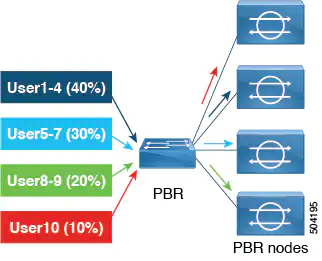
Beginning with Cisco APIC Release 6.0(1), weight-based symmetric PBR is supported, which handles traffic more efficiently. In weight-based symmetric PBR, an administrator can set weights for a PBR destination based on the capacity of the service node, and traffic is load balanced based on the set weights. One service node can be part of multiple policies and can have different weights in different policies.
Consider, four PBR destinations with different capacities. Instead of the same amount of traffic being sent to all destinations, PBR configuration for a destination is weight-based. You can assign a weight from 1 to 10. If no weight is assigned, the default value is 1. The assigned weight determines the traffic sent to the destination. An example of the weight-based distribution of traffic is shown below.
| Destination | Weight | Traffic % |
|---|---|---|
| Destination 1 | 4 | 40 |
| Destination 2 | 3 | 30 |
| Destination 3 | 2 | 20 |
| Destination 4 | 1 | 10 |
To maintain symmetric PBR on a two-arm node configured with weights, ensure to configure the same weight for the external and internal leg.
To maintain symmetric PBR for service insertion, where each service node has two interfaces, consumer and provider connectors, ensure to configure the same weight for both consumer and provider connectors.
Limitations of weight-based PBR
For PBR destination in a bridge domain, the maximum weight per PBR policy is 128. For PBR destination in an L3Out, the maximum weight per PBR policy is 64.
System faults are raised under the following conditions:
- Operational fault when the total weight of both primary and backup is greater than 128 (or 64 for L3Out) while programming in HAL/hardware.
- Configurational fault when the total weight of primary destinations is greater than 128 (or 64 for L3Out).
- Configurational fault when the total weight of backup destinations is greater than 128 (or 64 for L3Out).
Support for a user group map rule for SAML and OAuth 2
Authentication by an external server for SAML and OAuth 2 is based on user group map rule information, in addition to the standard CiscoAVpair-based authentication.

BGP autonomous system (AS) enhancements
Cisco APIC now supports the Remove Private AS option to remove private autonomous system numbers from the AS_path in an eBGP route and supports the AS-Path match clause while creating a BGP per-peer route-map.

Extended filter entries
In a SPAN session, you can now configure extended filter entries for filter groups by using either the APIC GUI, NX-OS-style CLI, or REST API.
Along with usual SPAN filter parameters such as Source/Destination IP Prefix, First/Last source port, First/Last destination port and IP Protocol, there's a way now to specify an extended filter entry that consist of:
- DSCP From - This field, together with the DSCP To field, specifies the range for filtering DSCP values
- DSCP To - This field, together with the DSCP From field, specifies the range for filtering DSCP values
- Dot1P From - This field, together with the DOT1P To field, specifies the range for filtering Dot1P values
- Dot1P To - This field, together with the DOT1P From field, specifies the range for filtering Dot1P values
- TCP Flags - TCP Flags pull-down menu
- Packet Type: Select the packet type. You can either select Routed/Switched, Routed, or Switched Only
You can either set the values for the Source/Destination range or the DSCP/Dot1P range. If you set both the Source/Destination and DSCP/Dot1P ranges, faults are displayed.
DSCP or Dot1p is not supported for the egress direction. If you select Both as the direction then either DSCP or Dot1p is supported for ingress direction only and not for egress direction.
TCP flags can be configured only if you have selected Unspecified or TCP as the IP Protocol.
Support for remote pools with a subnet mask of up to /28
Starting with the 6.0(1) release, remote leaf switches support remote pools with a subnet mask of up to /28. In prior releases, remote leaf switches supported remote pools with a subnet mask of up to /24. You can remove remote pools only after you have decommissioned and removed them from the fabric including all the nodes that are using that pool.

New hardware features
The new Cisco Nexus 9336C-FX2-E has been added as a leaf/spine option for your fabric. It has 36 x 40/100 Gbps QSFP ports supporting 1/10/25/40/50/100 Gbps port speeds or 16/32 Gbps FC ports with a total of 7.2 Tbps bandwidth and over 2.4 bpps. Breakout is supported on all ports.


Resolved issues
CSCvy00746
A breakout parent port shows in the drop-down list for the SPAN source even after the port is broken out.
CSCvz83636
For a health record query using the last page and a time range, the GUI displays some health records with a creation time that are beyond the time range (such as 24h).
CSCwa53478
After migrating a VM between two hosts using VMware vMotion, EPG does not get deployed on the target leaf node. When affected, the fvIfConn managed object corresponding to the missing EPG can be seen on APIC, but it would be missing from the target leaf node when queried.
CSCwa58061
When there are more than 40 objects in the tree and you double click on an object in the BGP Peer table, then the tree does not expand because the tree does not have pagination. The APIC tries to load all objects in one query, which is drastically slows the GUI
CSCwa78740
When HBR is enabled on a source EPG's bridge domain and the subnet is configured with the private scope (advertise externally = FALSE), if there is a shared service EPG contract with an L3Out, the L3Out will not publish the subnet or the corresponding /32 host routes because of this private scope.
In this scenario, if there is also an explicit ESG leakRoute configured for the same subnet across those VRF instances, the leakRoute is faulted because the route is already shared with an EPG contract, and the leakRoute is installed in the hardware along with a pcTag, then the leakRoute should not be processed and any flags under it should not be considered.
But, if this explicit leakRoute has a public scope, the /32 host routes are still published externally out of the L3Out, which should not happen as the leakRoute itself is faulted and bridge domain subnet scope is private.
CSCwa90058
When a VRF-level subnet <fvRtSummSubnet> and instP-level subnet <l3extSubnet> with a summary policy is configured for an overlapping subnet, the routes will get summarized by the configuration that was added first. But, the fault on the configuration that was added last will not be shown in the Cisco APIC GUI.
CSCwa95297
When a VRF-level subnet, fvRtSummSubnet, exists with a summary policy and an instP level subnet, <l3extSubnet>, with the same subnet as the VRF-level subnet is associated with summary policy, then there won't be any fault seen on the Cisco APIC. The summarization will be done according to the VRF-level subnet <fvRtSummSubnet>.
CSCwa99045
VMM domain attachments of floating SVIs configured for dual stack with the same encapsulation and the same VMM domain attachments are not being cleaned up after downgrading from 6.0(1) to an earlier release.
CSCwb00781
Importing the routing table of a remote site carries the wrong autonomous system number (ASN).
Compatibility information
Cisco NX-OS
16.0(1)
Cisco AVS
6.0(1)SV3(4.10)
Cisco UCS Manager
2.2(1c) or later is required for the Cisco UCS Fabric Interconnect and other components, including the BIOS, CIMC, and the adapter.
CIMC HUU ISO
- 4.1(3f) CIMC HUU ISO (recommended) for UCS C220/C240 M5 (APIC-L3/M3)
- 4.1(3d) CIMC HUU ISO for UCS C220/C240 M5 (APIC-L3/M3)
- 4.1(3c) CIMC HUU ISO for UCS C220/C240 M5 (APIC-L3/M3)
- 4.1(3b) CIMC HUU ISO for UCS C220/C240 M5 (APIC-L3/M3)
- 4.1(2g) CIMC HUU ISO (recommended) for UCS C220/C240 M4 (APIC-L2/M2)
- 4.1(2b) CIMC HUU ISO for UCS C220/C240 M4 (APIC-L2/M2)
- 4.1(1g) CIMC HUU ISO for UCS C220/C240 M4 (APIC-L2/M2) and M5 (APIC-L3/M3)
- 4.1(1f) CIMC HUU ISO for UCS C220 M4 (APIC-L2/M2) (deferred release)
- 4.1(1d) CIMC HUU ISO for UCS C220 M5 (APIC-L3/M3)
- 4.1(1c) CIMC HUU ISO for UCS C220 M4 (APIC-L2/M2)
- 4.0(4e) CIMC HUU ISO for UCS C220 M5 (APIC-L3/M3)
- 4.0(2g) CIMC HUU ISO for UCS C220/C240 M4 and M5 (APIC-L2/M2 and APIC-L3/M3)
- 4.0(1a) CIMC HUU ISO for UCS C220 M5 (APIC-L3/M3)
- 3.0(4l) CIMC HUU ISO (recommended) for UCS C220/C240 M3 (APIC-L1/M1)
- 3.0(4d) CIMC HUU ISO for UCS C220/C240 M3 and M4 (APIC-L1/M1 and APIC-L2/M2)
- 3.0(3f) CIMC HUU ISO for UCS C220/C240 M4 (APIC-L2/M2)
- 3.0(3e) CIMC HUU ISO for UCS C220/C240 M3 (APIC-L1/M1)
- 2.0(13i) CIMC HUU ISO
- 2.0(9c) CIMC HUU ISO
- 2.0(3i) CIMC HUU ISO